What is PCI (PCI_DSS) compliance?
PCI stands for Payment Card Industry (Amex, Visa, Mastercard, Discover, etc). PCI_DSS stands for Payment Card Industry Data Security Standard.
The payment card industry requires anyone who deals with payment card information to be compliant. That is, the industry requires people who handle the customers’ credit card information to be responsible for the security of that information thus preventing credit card fraud. Sort of like how Sarbanes Oxley compliance makes big companies responsible for their accounting thus preventing white-collar fraud (Enron et al).
Who needs to be PCI_DSS compliant?
Any merchant who stores, processes or transmits credit card information needs to be compliant.
Why should I care about it?
How would you feel if you used your credit card to make an online purchase and your credit card information was stolen because the online vendor was careless in handling your credit card information? You would want any fraudulent transactions on your credit card to be removed right?
If you as a vendor are not PCI_DSS compliant then you have not done enough to be responsible for any customer credit card information you may have stored, processed or transmitted. And if some miscreant steals this information to make fraudulent transaction then:
- You lose the goodwill of that customer (not to mention a really pissed off customer may go viral with the experience, causing much more damage)
- The credit card company can hold you liable for all these fraudulent transactions (If several credit cards have been breached, this liability can add up and drive your company bankrupt)
You may be tempted to think that the likelihood for this theft from your web-store is low given that it has not happened before. But this scenario is comparable to identity theft: May not have happened to you yet, but when it does it is extremely frustrating and time consuming to secure it again. Not to mention that hackers are getting increasingly efficient in writing malicious code that automatically scans the internet for such vulnerabilities and attacks them.
When do I need to be compliant?
Compliance in general requires two activities:
- Quarterly: Getting a vulnerability scan from an Approved Scan Vendor (ASV)
- Annual: Self Audit or external audit by a QSA
Where do I go to get more info?
https://www.pcisecuritystandards.org/
How can I be compliant? (OR How to avoid it altogether!)
Let look at the easier way out first. If you wash your hands off (outsource) all credit card storing, processing and transmitting activities you can be spared of all this!
There are multiple services that will do this for you:
- Checkout services: Google checkout, paypal, et al
- Shopping carts: Yahoo Stores, Shopsite, volusion, bigcommerce are some service providers who manage the credit card transactions for you
Of course there is no such thing as free lunch. You may have to give up on some user experience and/or incur some cost. For example sending your customer to another website, unable to offer one click checkout or simply paying the outsourcing service a cut of your revenues.
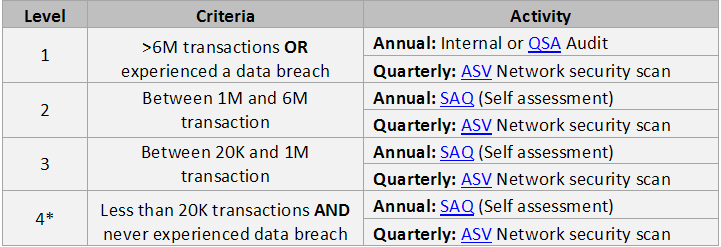
If you don’t want to make these trade-offs then here’s a cheat sheet to help you understand what “merchant level” you are and what you need to do to be compliant:
*In addition, the credit card issuer/processor of “level 4 merchants” may ask for a summary compliance plan; which, in-turn will have to be consolidated by the issuer/processor and sent to the PCI.
Why this extra burden on low transaction merchants?
Apparently these merchants account for 99% of all credit card transactions and at the same time are the most vulnerable to hackers due to lack of IT security expertise. Credit card companies report
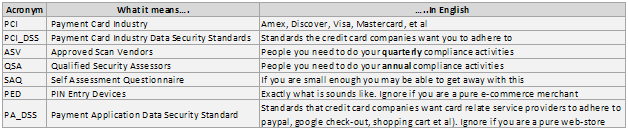
Jargon
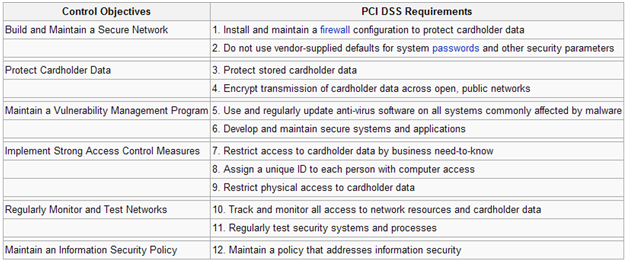
This is what the compliance is trying to achieve: (Of course if you love pdfs here’s the detailed version)